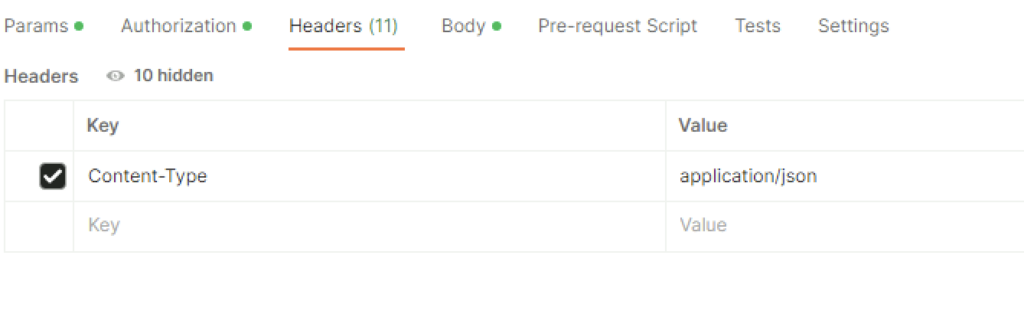
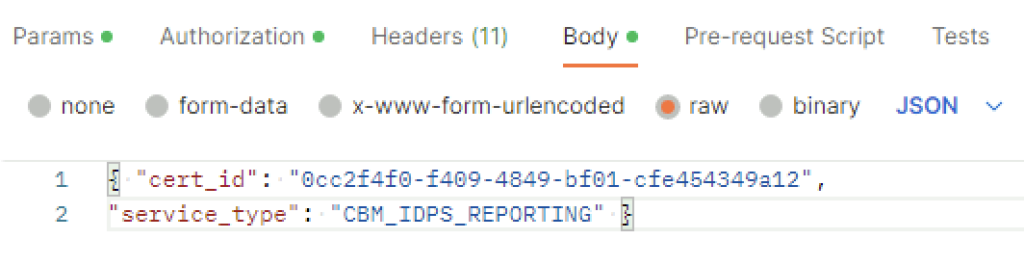
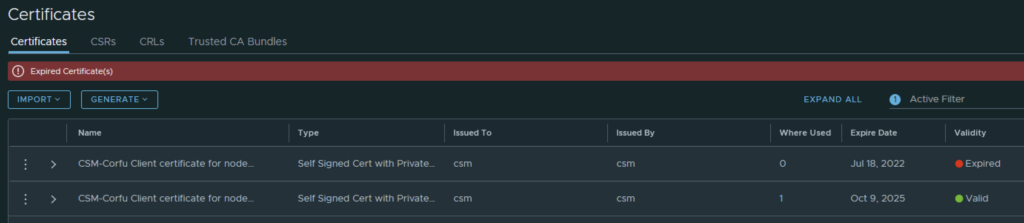
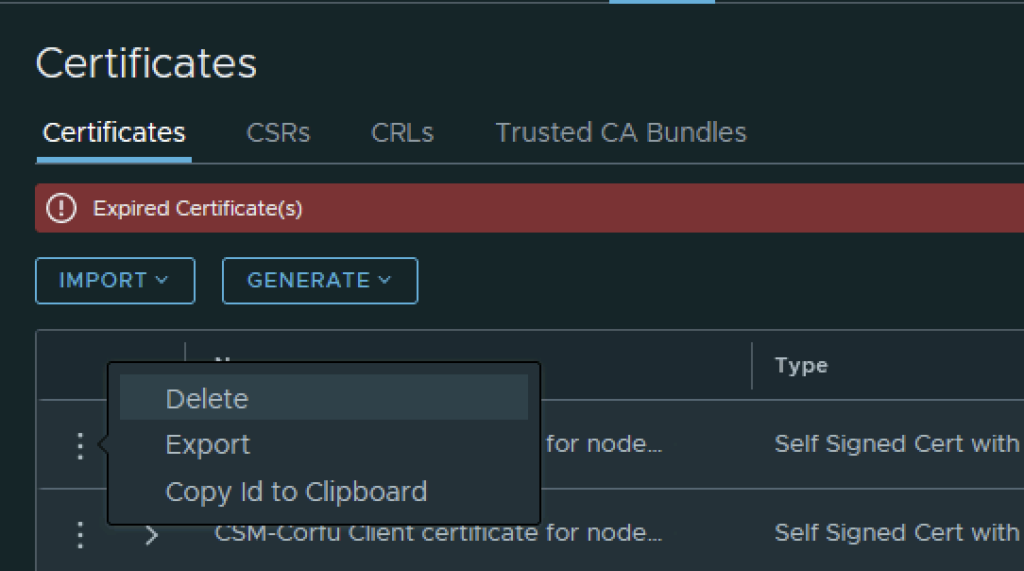
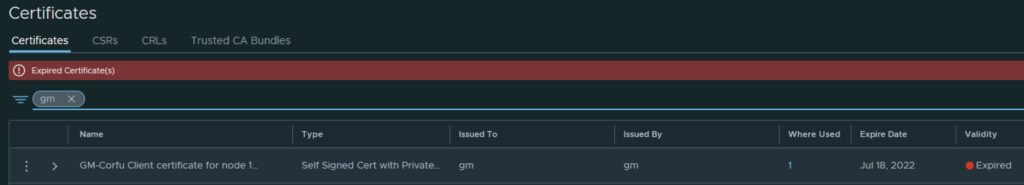
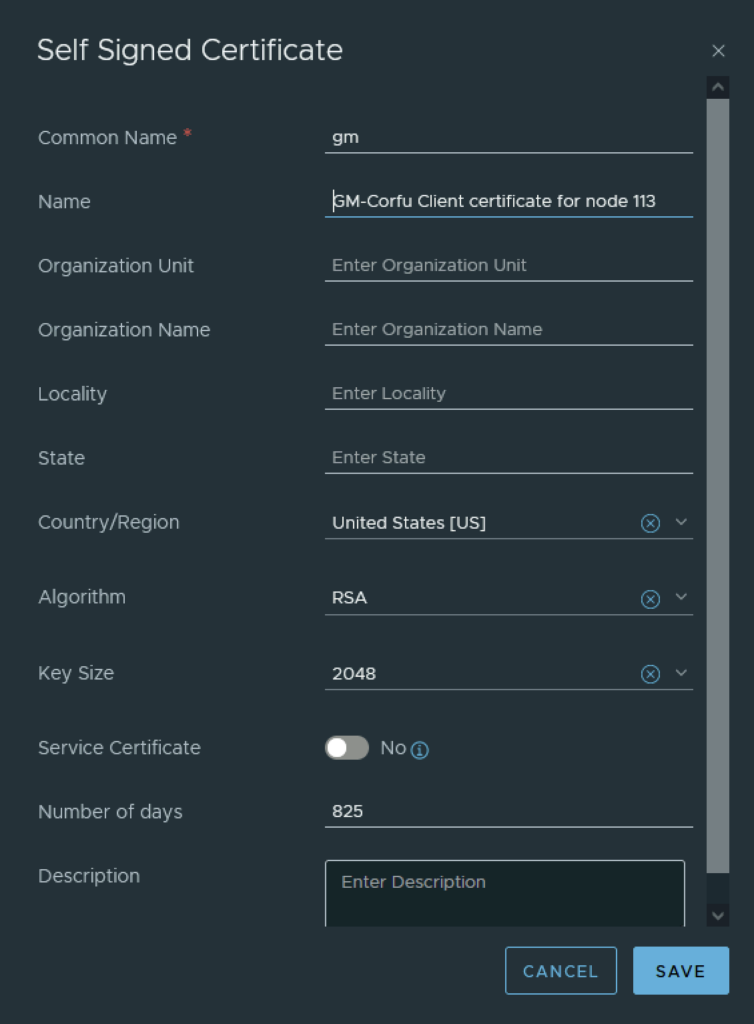
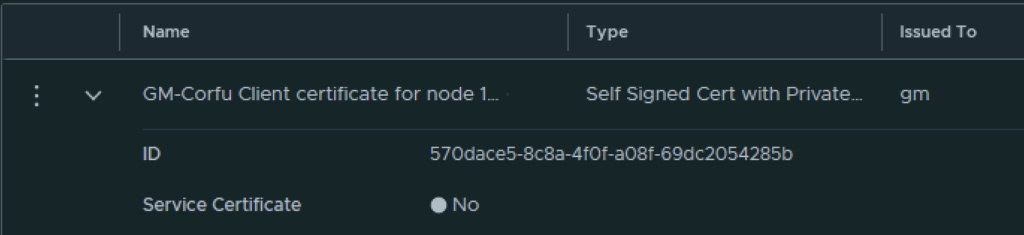
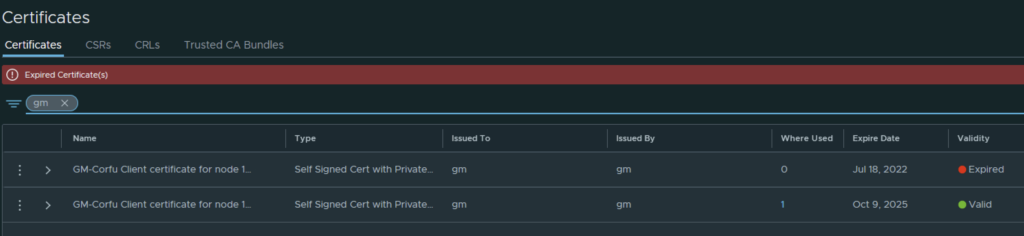
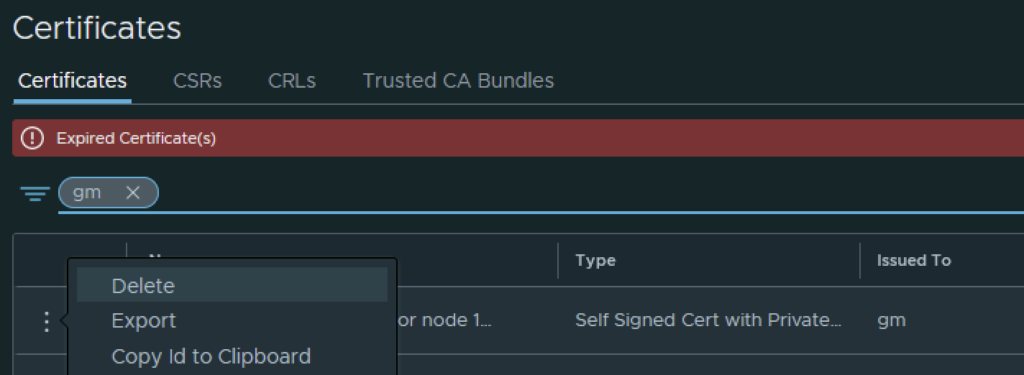
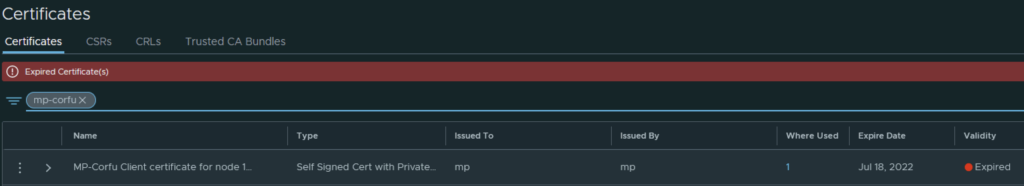
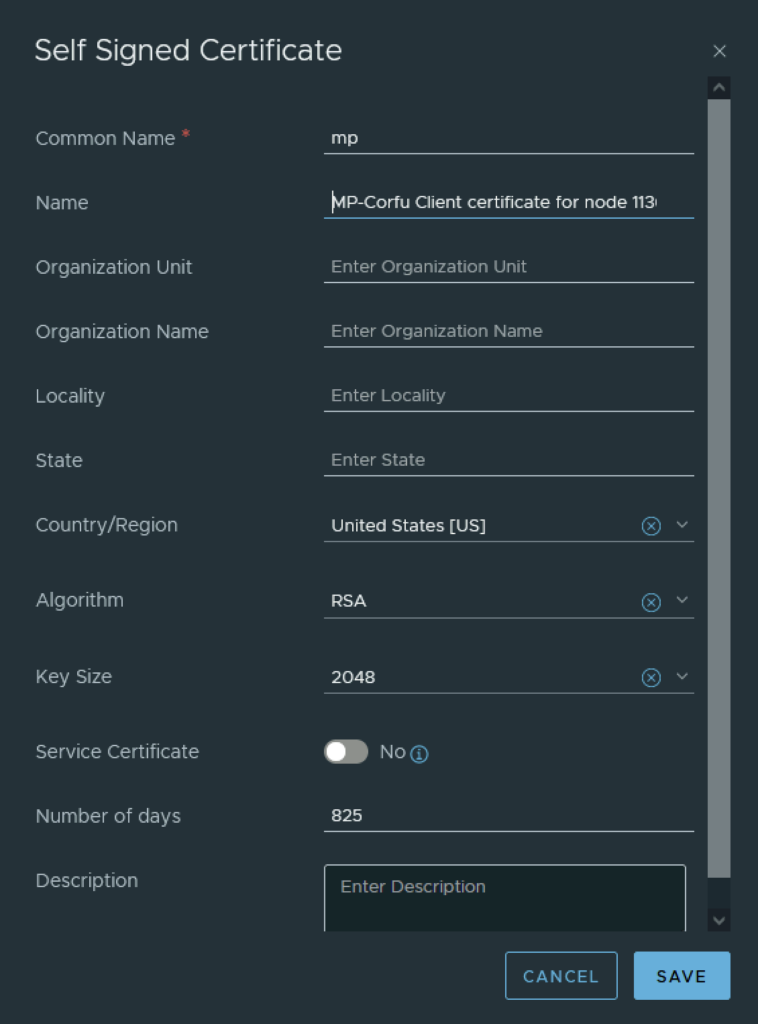
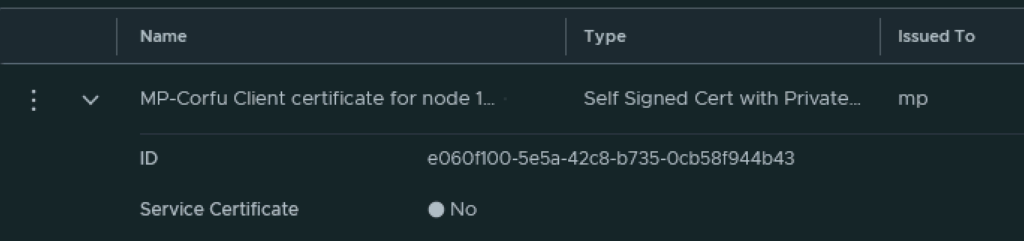
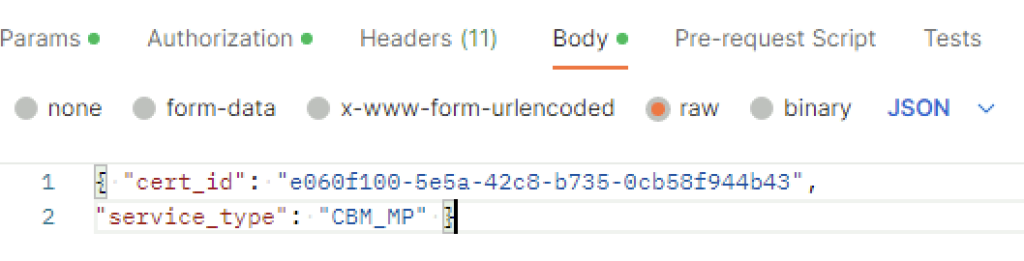
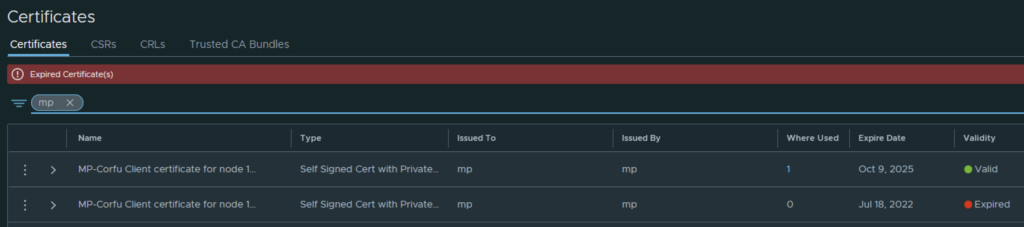
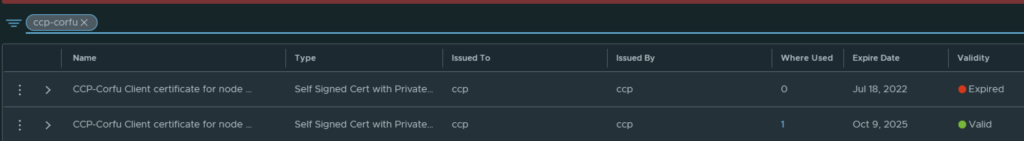
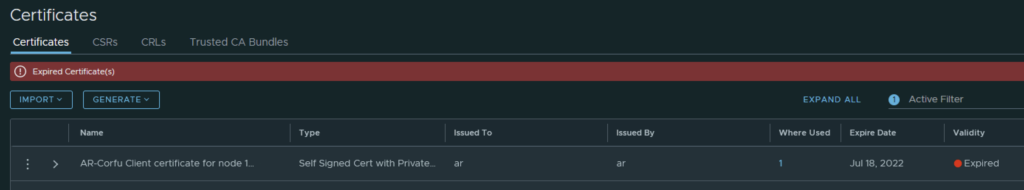
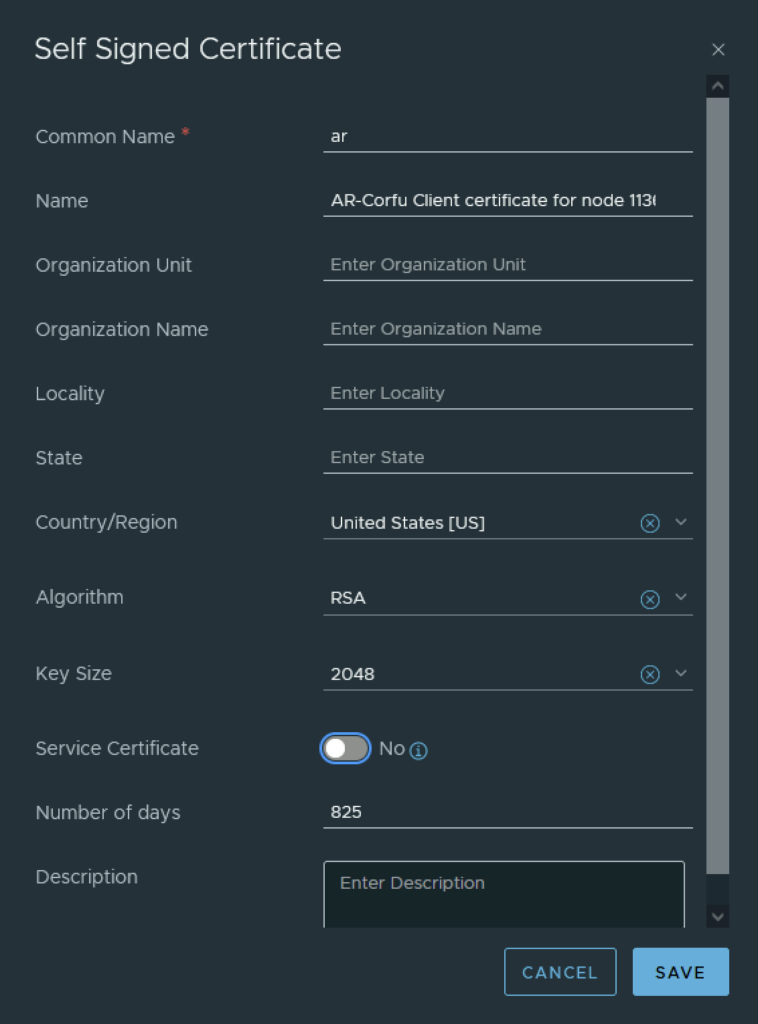
In VMware NSX, configuring SSH keys for users with specific labels and types provides a tailored access control approach that enhances both security and management capabilities. This blog walks through the process of setting user-specific SSH keys in NSX, using customized labels and types for better organization and identification.
Overview
SSH keys are crucial for secure authentication in NSX environments, allowing administrators to manage access without exposing systems to the risks of password-based logins. By setting SSH keys with specific labels and types, you can streamline user access management and improve security configurations.
Prerequisites
Ensure you have administrative access to the NSX Manager and that the users have generated their SSH key pairs. You will need the public key, and an understanding of the user’s role and required access level within NSX.
Step 1: Prepare the SSH Key Information
Collect the following information for each user:
- User ID: The identifier for the user in NSX.
- Label: A unique label to identify the key’s purpose or the user’s role.
- Type: The encryption type of the SSH key, typically RSA or ECDSA.
- Public Key: The actual public key string.
Example format:
set user [USER] ssh-keys label [LABEL] type [TYPE] value [PUBLIC KEY]Step 2: Access the NSX Manager CLI
Connect to your NSX Manager via SSH or through the direct console interface. You will need to use the administrative credentials to log in.
ssh admin@nsx-manager-ipStep 3: Add the SSH Key
Once logged in, you can add the SSH key for the user. Replace [USER], [LABEL], [TYPE], and [PUBLIC KEY] with the actual values. Here’s an example command:
set user jdoe ssh-keys label admin-access type rsa value "AAAAB3NzaC1yc2EAAAADAQABAAABAQC..."This command sets an RSA key for user jdoe with the label admin-access.
Step 4: Verify the Key Setup
After adding the SSH key, verify that it has been correctly set up by listing the SSH keys for the user:
show user jdoe ssh-keysThis command should display all SSH keys associated with the user, including the newly added key with its label and type.
Step 5: Test SSH Connectivity
Have the user test their SSH connectivity to ensure that the key works correctly:
ssh -i /path/to/private/key jdoe@nsx-manager-ipIf the setup is correct, the user should be able to connect without a password prompt, indicating that the key has been accepted.
Conclusion
Setting user SSH keys in NSX with specific labels and types is a powerful way to enhance your network security and streamline access management. By organizing SSH keys in this manner, you can easily maintain control over who accesses what within your NSX environment, ensuring that only authorized users can perform administrative tasks.